Nillion 101 🛡️
A Secure Processing Layer for Web3
BIG ANNOUNCEMENT
Launched FutureX’s closed discord, some good investor friends are already in :)
If you’d like to join in, please reach out to me on Twitter at @DarshanG_
Today we are talking about 👇
Nillion
What will we be covering today?
What is Nillion building?
Introduction
Historical comparison between: ZKP vs SPMC vs NMC
All about Nil Message Compute
Summary
One-time Mask
Linear Secret Sharing
Main roles in the network and details about each of them
Steps for computation in the network
Different forms of NMC protocol
Comparative analysis based on communication complexity
Bandwidth consumption of SMPC protocol & issue with it
Comparison based on execution: SMPC vs NMC
Security
Processing part of Nillion’s product
The Nillion Network
Architecture
Infrastructure layer
NMC layer
Service layer
Permissionless nodes
Nillion Token
Team behind the technology
Core use-cases or applications
Distribution & GTM Strategy
Closing thoughts & how to get involved
⚒️ What is Nillion building?
Nillion is building a secure processing layer of web3
Nillion allows nodes in a decentralised network to work in a non-blockchain way - to expand the capability of these nodes beyond the blockchain.
They’re building a new cryptographic primitive named “Nil Message Compute“ which paves the way for decentralized processing, storage, and data, both for existing blockchains and as a native public utility in a secure manner
I’ll talk about NMC in detail in the below sections 👇
🏁 Introduction
Over years, the need of parallel processing and decentralisation has been on the rise.
Technologies like blockchains and secure multi-party computation (SPMC) have developed to solve these issues.
Blockchain enables a common ledger to be shared across decentralized networks
SMPC is built for processing and computation within a trustless environment
Let’s talk about the principles of SMPC:
Information-Theoretic Security (ITS) based - a security that is cryptoanalytically unbreakable
Distributed computation between trustless nodes
But the major issue of SMPC is that of scalability due to internode-messaging, which takes A LOT of time to process
Nillion is created by combining the strength of SPMC and Blockchains, enabling a cutting-edge (non-blockchain, non-traditional SMPC) network that can deliver decentralised computing to blockchains and developers at speeds that are nearly client-server fast.
There are several applications outside of the financial segment where it can be used like:
NFTs
Play-to-Earn games
DAOs
Identities
Social Media & many more
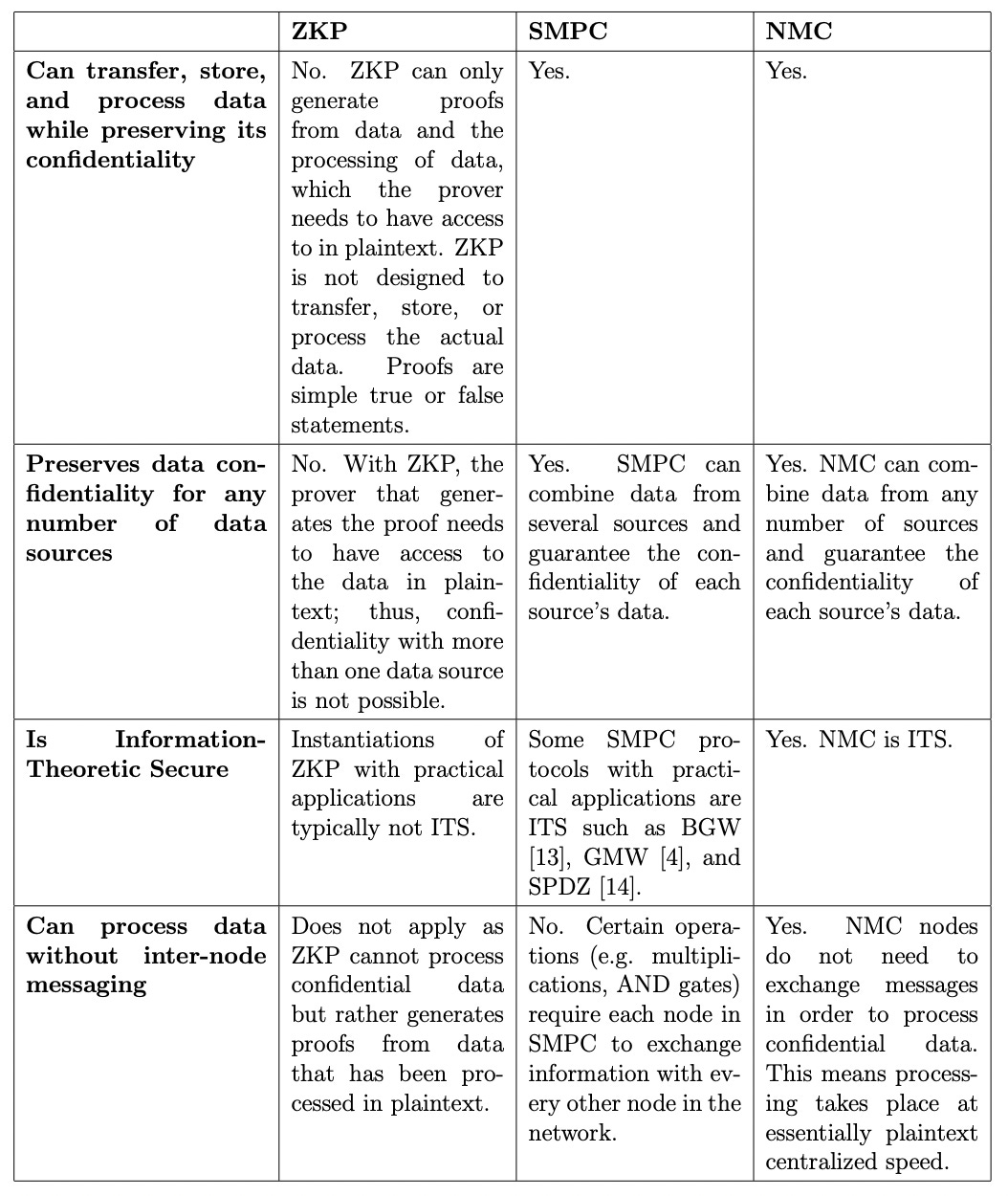
👀 Historical comparison: ZKP vs SPMC vs NMC
Let’s first of all learn about each one of them
ZKP:
ZKP is currently the main cryptographic primitive providing privacy to blockchain technology, and it underpins many significant privacy tokens and private smart contract enabled protocols.
ZKP allows a node (the “prover”) to prove to another node (the “verifier”) that a given statement based on the data they hold is true without sharing this data.
SMPC
Secure Multi-Party Computation is an application of advanced mathematics to enable crypto assets to be stored, transferred, and deployed more securely, easily, and flexibly than ever before.
Processing confidential data in an SMPC network requires the nodes to exchange a large number of messages when the computation is not trivial.
NMC
NMC is the cryptographic foundation underlying Nillion, it allows for the implementation of a decentralized, private, performant, ITS, and versatile public network
Here’s a tabular difference between the three:
🔥 Nil Message Compute (NMC)
Cool, let’s dive deeper into NMC and understand what exactly is it.
Summary:
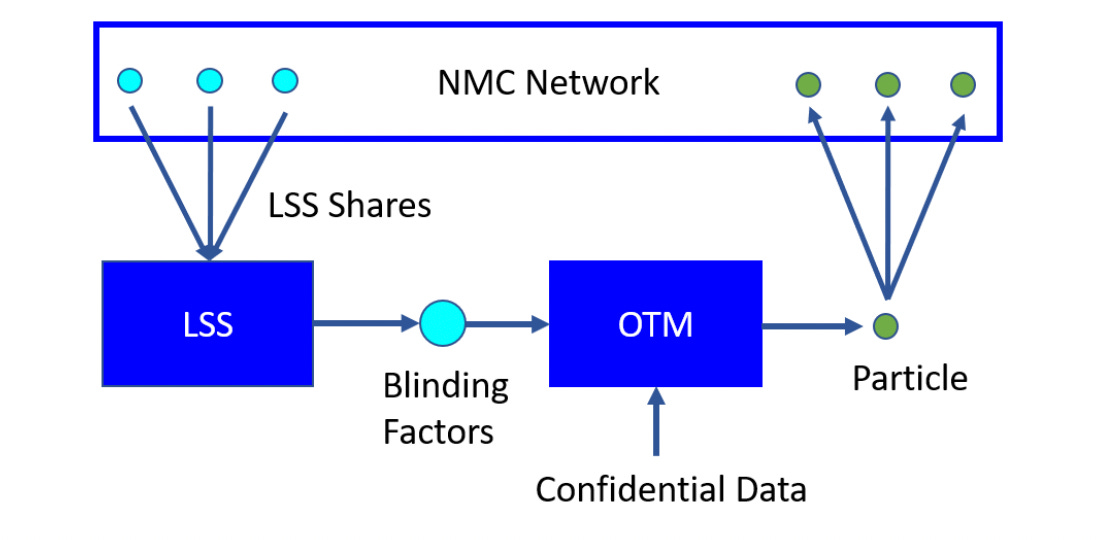
Nillion uses and combines two ITS cryptographic building blocks. The first is a One-Time Mask (OTM), which transforms a secret into a particle by making use of random blinding factors.
The second is Linear Secret Sharing (LSS) based on a threshold of T + 1, which transforms the blinding factors into shares distributed among Nillion nodes.
Now, let’s go into the detail of understanding each term and concept 👇
Let’s talk about each of them:
One-Time Mask
OTM is an ITS cryptographic primitive that makes use of a series of random numbers called blinding factors to mask a secret, similar to one-time-padding or ITS Message Authentication Codes
OTM is designed to deliver correctness with efficiency, meaning NMC Nodes are not required to exchange any messages to perform a computation.
Linear Secret Sharing
LSS is a cryptographic primitive that transforms a confidential statement into N numbers called shares.
The N shares are distributed across N SMPC nodes such that: • Every node gets a unique share
Any group of T + 1 nodes (where T + 1 ≤ N) can reconstruct the confidential statement, and
Any colluding group containing strictly less than T +1 nodes cannot deduce anything from the shares they hold.
Some of the SMPC protocols also are based on LSS. Here’s how the steps look:
Step1: The inputs to the computation are transformed into shares, which are distributed across the SMPC nodes.
Step 2: The actual computation takes place, which typically involves the exchange of messages between the SMPC nodes. At the end of this step, every node will have a share from each one of the computation output values
Step 3: The result shares are sent to one or several Result Nodes, which run LSS to reconstruct the outputs.
Now, the scalability problems of SMPC is seen primarily in the second step, where there’s a need for inter-node messaging.
So, Nillion, combines OTM & LSS into one technology - NMC, where OTM can be optimized for both correctness and efficiency, removing the need for NMC’s to keep exchanging messages between nodes, like it’s needed to be done in SMPC.
Here’s how both primitives work in practice together:
Next, let’s learn about the different components of the NMC Network.
The main roles in the network are:
Dealer Nodes
These are nodes that transform their confidential and private inputs to the NMC computation into particles and distribute them across the NMC Nodes.
For instance, a Dealer Node can be an individual using their mobile device, or a corporation using a company server
NMC Nodes
These nodes store the particalized inputs provided by Dealer Nodes and perform the actual NMC computations on them.
Result Nodes
These nodes reconstruct the results from a finished NMC computation.
Let’s go through the flow:
Step 0 - Pre-Processing
The NMC Nodes generate portions of the blinding factors required by the OTM cryptographic primitive as part of the pre-processing step.
These calculations can be performed in advance hours, days, or even months before they are really required because they are not dependent on the private inputs of any specific NMC execution.
Step 1 – Particle Distribution
In this step, every Dealer Node conceals every private input using a separate blinding factor with an ITS OTM.
During the pre-processing phase, the NMC Nodes create the blinding factors necessary to hide the private input, and the Dealer Nodes rebuild them using the LSS shares they receive.
Step 2 – Computation
After Step 1, each NMC Node contains one particle from each private input to a computation.
The computation consists of evaluating the output of a function over the private inputs.
To achieve this, the NMC Nodes perform local multiplication and addition operations on their particles as dictated by the arithmetic function that needs to be evaluated.
Thus, there’s no need for inter-node communication
Step 3 – Result Reconstruction
After Step 2, each NMC Node will have obtained a particle from the result of the computation
Each node sends its particle and the blinding factor shares to one or several Result Nodes
Then, each Result Node runs NMC’s Reconstruction Mechanism to obtain the output of the function that was jointly evaluated
Nillion has two different types of the NMC protocol, both with the key property of allowing for fast computations without inter-node communication:
2-NMC:
allows a network of NMC Nodes to evaluate any function with private inputs coming from 1 or 2 Dealer Nodes.
This function can be expressed as an inner product of two A-dimensional vectors, where A is the number of additions in the computation.
D-NMC:
allows a network of NMC Nodes to evaluate any function with private inputs coming from any number D of Dealer Nodes.
This function can be expressed as a sum of the products of confidential input values.
Here’s a breakdown a performance comparison in terms of communication complexity 👇
As the server size increases, more and more nodes come into the picture, hence for a SMPC to keep up and perform well, a large number of inter-node messages need to be exchanged.
Now, as the number of messages increase, so would the network bandwidth consumption. Check out the graph below for reference 👇
From an execution time standpoint:
In state-of-the-art SMPC, every multiplication requires the exchange of 2N2 messages in a network with N nodes.
In NMC, it involves a local multiplication between particles that requires no message exchange.
Here’s a diagram to understand it better
Almost 28hrs are being saved and getting the same process done - that’s a massive massive time saver
Security is obviously at the heart of what Nillion’s building and advocating for:
Confidentiality: Data and computations are confidential.
Integrity: Data is protected from unauthorized changes. Data and computations are reliable and correct.
Availability: Resources are always accessible to authorized users even in the event of node failures
Let’s understand about the processing side of things, because that’s what is the “juicy“ part of Nillion’s product
Compile Time
At compile time, Nillion and the community will develop services that process data on the network using a Developer Node
NMC will support high-level programming languages that will be compiled into an arithmetic circuit representation of the computation in bytecode
An IDE will also be provided to the developers for creating stuff on their own - they can use standard libraries or create their own abstract and reuse code
Runtime
At runtime, the network of NMC Nodes will run services on particles created from real data.
An NMC Node comprises an API to receive MPPs, particles, and shares.
At the core of an NMC Node are its main processing components:
Data storage module for particles and shares
Service storage module for MPPs.
Runtime VM that runs on the storage and network layers
Particles and shares have their own Create, Read, Update, and Delete (CRUD) module that is used when the NMC Node acts as a Dealer Node or as a Result Node.
Client applications interact with the NMC Nodes by using an NMC SDK which computes input particles from sensitive data and reconstructs processing results from output particles.
The use of an SDK to intermediate end-user interactions with the NMC network as opposed to an API is central to Nillion’s security model.
🌎 The Nillion Network
Till now we’ve learnt about the NMC protocol and analyzed its performance, decentralized nature, and security features.
We shall now talk about
Three main layers comprising the network’s foundational architecture
Main attack vectors on NMC such as Sybil attacks, bribery, and collusion between nodes + how NMC works on protecting against these
The important role of the NIL token in the Nillion Network, including node incentives, staking, network security, and decentralized governance
Architecture
Nillion’s network architecture comprises three layers: the Infrastructure Layer, NMC Layer, and Service layer. Let’s learn about each of them.
Infrastructure Layer:
The network and storage infrastructure in the Nillion Network builds on a Distributed Hash Table (DHT)
The underlying peer-to-peer network has the properties of being: decentralised, resilient, support LSS, support other storage forms
NMC Layer:
The NMC Layer implements our two proprietary protocols: 2-NMC and D-NMC.
These protocols are able to run Multi-Party Programs without any message exchange during the computation step
The NMC Layer implementation is secure, exhibiting high availability, confidentiality, and integrity.
NMC will offer three core capabilities to developers through an SDK: transfer, store, and compute
Nil Service Layer:
The Nil Service Layer builds on top of this via Nillion’s MPPs to provide additional services.
These services will be used by Nillion to implement the initial use cases showcasing the network’s capabilities and can be further extended by the developer community.
To do so, Nillion will offer its own high-level programming language called Nada, and may support additional existing languages, such as Solidity
A few of the key services that would be supported by the service player are:
Authentication: Offers various out-of-the-box methods for authenticating and authorizing user operations using MFA.
Key management: Offers different functionalities around the storage, transmission, and processing of digital certificates and keys.
Enrollment: Offers decentralized Know-Your-Customer (KYC) and Know-YourBusiness (KYB).
Voting: Offers decentralized anonymous voting with configurable quorum and majority definitions, as well as definable rules that can be used, for instance, to automate governance functions in DAOs.
Permissionless nodes & possible attacks on them
Nillion is a permissionless network supporting two types of NMC Nodes:
Light Nodes: These transfer, store, and process particles from the data. Particles are public.
Full Nodes: These transfer and store shares from the blinding factors, and also transfer, store, and process particles from data. Shares are private.
What’s a Sybil Attack?
It’s a single entity pretends to be multiple independent nodes, hoping to be assigned all the shares for a data asset so as to be able to reconstruct it.
To prevent Sybil attacks against Full Nodes, node operators will be required to stake a certain number of NIL tokens in order to participate in the storage of shares and calculations.
With NMC’s mechanism of requiring a sign from T+1 nodes to move ahead, as the network grows, the chance that a group of malicious nodes will receive a sufficient number of shares to reconstruct blinding factors will approach zero.
For example, in a network with 100 Full Nodes, a bad actor who controls 51 Full Nodes poses a threat. However, the same bad actor is impotent in a network of 10,000 Full Nodes.
The NIL Token
The NIL token will be Nillion’s native utility token. NIL will initially be implemented using Ethereum’s ERC-20 standard.
NIL tokens will be used to:
Access the network and use various Nillion services.
Align economic incentives and node cooperation through staking.
Incentivize nodes to maintain high performance and uptime.
NIL tokens will also play a key role in the governance of the network through the Nillion Decentralized Autonomous Organization (nilDAO).
💰 Applications
Amazing, so we’ve learnt about what’s up with Nillion and the tech aspects of things - but now let’s also understand more from a practical standpoint how does it exactly work.
The Nillion network will be developed in three phases:
Phase 1: Will comprise the development of a secure, public network for the storage and use of private information
Phase 2: Will focus on the development of a Meta Layer that enables the Nillion Network to enhance and connect different blockchains, thus providing interoperability and cross-chain computation solutions.
Phase 3: Will be the implementation of the final vision of Nillion – the secure processing layer
Let’s dive into the different applications and use cases:
Interaction with centralised wallets:
One iteration of using the authentication services would be the integration of this private key storage solution within a crypto wallet
The wallet would then be able to sign transactions on behalf of the user without needing the private key to be held on a device or centralized server
Storing official documents:
Nillion’s infrastructure can be used to store documents such as identity documents, deeds, wills, titles, contracts, and agreements.
Individuals will be able to link these documents to a set of decentralized authentication factors, whereby only the individual will be able to access or edit the contents.
Furthermore, official purchasing documents such as deeds or other entitlements could be transferred between parties without the need for an intermediary
Similarly, businesses can store data such as customer 42 data, secret formulas, trade secrets, and any other intellectual property
Private smart contracts on public blockchains:
One key use case is the enabling of decentralized private smart contract compute and a secure execution environment for public blockchains
Here’s an example:
The user writes the smart contract in Solidity.
The user sends it to Nillion for execution.
The user also sends a hashed version of the inputs to Nillion’s smart contract in Ethereum.
The smart contract is executed in Nillion with full confidentiality.
Interoperability:
Nillion will enable blockchain interoperability solutions to allow for the transmission of assets, events, and data.
Advanced cross-chain solutions become possible when built on NMC-enabled interoperability schemes.
Multi-Party Programs running in the Meta Layer could be used to link complex systems that span chains and protocols, providing support for
bridges
liquidity aggregators
cross-chain decentralized exchanges
A unified multi-chain wallet with ITS authentication:
Nillion enables a true multi-chain wallet by allowing a user to securely store all the private keys from different blockchain wallets in a single, completely decentralized, Nillion account or wallet
The keys are kept in particalized form so that an attacker would have to compromise an unfeasibly large proportion of all Nillion nodes in order to piece them back together.
Gated NFT metadata and content:
The privacy and granular control of access to secure information enabled by Nillion’s design unlocks the next generation of use cases for NFTs on any chain.
When tokens point to data hosted in the network, Nillion can offer tools to gate access to the metadata or underlying content, providing minters and owners the ability to decide who can see or interact with their property
DAO tools:
DAO tools represent another use case that takes advantage of the Nillion Network’s privacy features.
NMC can support decentralized anonymous voting through the creation of a voting core service.
The network can also help DAOs manage private information.
🤼 Team behind Nillion
The team behind Nillion have founded several billion-dollar crypto and non-crypto companies together, including two of the top 100 cryptocurrencies.
Chief Scientist Dr. Miguel de Vega is the Inventor of NMC and has authored over 30 patents in the fields of machine learning, data optimization and mathematics.
CTO Conrad Whelan was the Founding Engineer of Uber. ● Head of Cryptography Dr. Elizabeth Quaglia is a senior lecturer at Royal Holloway, University of London, one of the world’s leading cryptography institutions.
CEO Alex Page is a seasoned ex-Goldman Sachs investment banker.
Director of Crypto Tristan Litré was previously CTO of a DeFi platform and is an avid crypto-native DAO contributor.
Chief Business Officer Slava Rubin was the Co-Founder and CEO of Indiegogo.
CMO Andrew Masanto previously started Hedera Hashgraph and Reserve.
Those are some top top tier folks in the team - it’s looking very exciting!
💡 Distribution and GTM strategy
Obviously the team realises that it’s good to have things sounding great in theory, but only can be validated once they’re found working in practical scenarios and growth is seen - distribution and adoption is going to be the key.
A few key initiatives being worked upon by the team are:
Founding Entrepreneurs will form part of the early-stage protocol development team and they’d provide internal feedback loops and advise to the development
An SDK for third-party developers to create additional applications
Referral-based programs - ah this one cooks well :)
💭 Closing thoughts & getting involved
Overall I have really enjoyed going through the whitepaper or rather I’m not wrong if I call it a “research paper“.
Security and fast processing are going to be at the core of driving the future of communication be it on-chain or off-chain - services like NMC are going to be a game changer for driving such growth.
Obviously, if you find it what you’ve read to be interesting or want to learn more. You can reach out to me on Twitter and I’d be happy to make an introduction.
Please check out the the relevant links to learn more about the project:
Phewww!!! That’s all, fam; I hope it was a great time reading! Please do leave a like if you did :)
It’s a very new ecosystem for me to learn and read about - if you’ve made it till here, I AM BEYOND GRATEFUL - happy to hear any feedback / thoughts you’d have :)